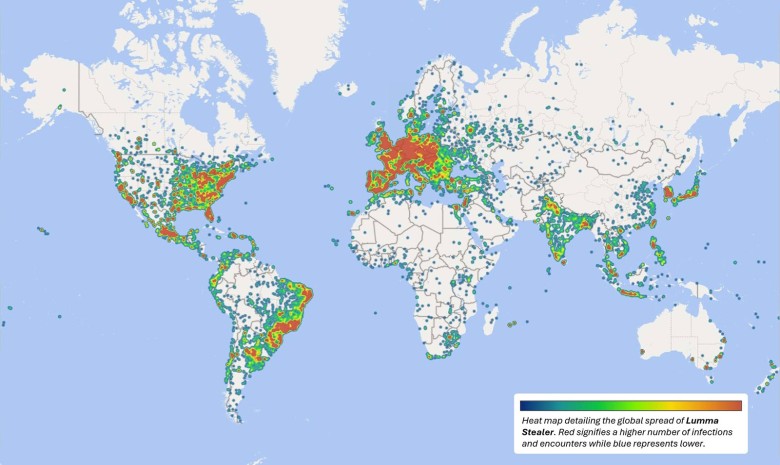
Microsoft, in collaboration with law enforcement agencies, has executed a court-authorized takedown of Lumma, a widespread information-stealing malware operation, TechCrunch reports. The malicious software was discovered on over 394,000 Windows PCs globally, with a significant concentration of infections in Brazil, Europe, and the United States.
In a significant blow to the cybercriminal network, the tech giant pursued civil action, leading a federal court to order the seizure of approximately 2,300 domains. These domains formed the critical command and control infrastructure for the Lumma malware. Concurrently, the U.S. Department of Justice seized an additional five domains integral to Lumma's operations.
The Lumma password stealer typically infiltrates systems when users download compromised software, such as dubious games or cracked applications, from the internet. Once active, the malware exfiltrates a wide range of sensitive information from victims' computers, including login credentials, passwords, credit card details, and cryptocurrency wallet information. This stolen data is then often sold to other malicious actors on cybercrime forums.
Beyond its data theft capabilities, Lumma also functions as a backdoor, providing hackers with an entry point to deploy further malware, including destructive ransomware.
Security experts have highlighted the growing threat of password-stealing malware like Lumma. Such malicious tools have been implicated in significant cyberattacks that resulted in the theft of vast quantities of data from various companies, including notable incidents involving tech firms PowerSchool and Snowflake. The takedown of Lumma's infrastructure marks a crucial step in disrupting the broader cybercrime ecosystem that relies on stolen credentials.
Total views: 534